Active Directory
What is Active Directory?
Active Directory (AD) is a directory service developed by Microsoft for Windows domain networks. Windows Server operating systems include it as a set of processes and services. A domain controller (DC) is a server running the Active Directory Domain Service (AD DS) role. It authenticates and authorizes all users and computers in a Windows domain-type network, assigning and enforcing security policies for all computers and installing or updating software.

A directory service consists of both a directory storage system called the “directory store” and a mechanism that is used to locate and retrieve information from the system. The directory service's primary functions are managed by the Directory System Agent (DSA), which runs on each domain controller.
Active Directory stores objects that provide information about the real entities that exist in an organization’s network such as printers, applications, databases, users etc. Active Directory can be associated with one or more domains. It stores information about users, specific groups of users like the Administrator, computers, applications, services, files, and distribution lists etc. Active Directory then makes this information available to the users and applications throughout the organization.
Active Directory is a key component of the Windows environment. In Azure environments, Azure Active Directory (Azure AD) performs a similar function. Like other Windows services, its performance can affect the rest of the target environment. Active Directory consumes system resources, and the administrator needs to be conscious of long-term resource usage to plan for future capacity upgrades.
Gathering performance data gives AD administrators an effective way to see the effects of any optimization efforts that they might attempt and provides information for diagnosing problems when they occur (see: Active Directory Troubleshooting (eginnovations.com) for more information).
Most Windows servers and components are dependent on Active Directory either directly or indirectly, especially on-prem. So, monitoring the Active Directory server’s performance regularly is necessary to make sure that the target environment is meeting your business and networking goals. This is where eG Enterprise can help administrators.
In cloud environments Azure Active Directory (Azure AD) is often leveraged to perform a similar role to Active Directory. It is also common for Azure AD and Active Directory to be used together with Azure AD Connector, especially in organizations following hybrid cloud strategies. For those looking at hybrid cloud configurations and how to replace or integrate Active Directory into such a setup, you may like to explore: Hybrid without hybrid – this is the way! – Digital Workplace Blog- an insightful community blog exploring many issues around Active Directory and hybrid infrastructures.
What are the key components of Active Directory?
The key components of Active Directory include:
How does Active Directory work?
Active Directory works by providing a centralized and standardized system for managing network resources and enabling secure authentication and authorization. Here's an overview of how it operates:
AD is implemented on one or more servers known as Domain Controllers. These servers store the AD database, which includes information about users, computers, and other resources. When a user logs into a computer within the AD domain, their credentials are sent to a DC for verification. The DC checks the credentials against the AD database and, if valid, allows the user to access network resources.
Once authenticated, AD uses Group Policies and security groups to control what resources users can access and what actions they can perform. This ensures that users only have access to what they are permitted to. AD uses a multi-master replication model to ensure consistency across all Domain Controllers. Changes made on one DC are replicated to others, ensuring that all controllers have up-to-date information.
Multi-master replication in Active Directory
A multi-master enabled database, such as the Active Directory, provides the flexibility of allowing changes to occur at any DC in the organization. However, this also introduces the possibility of conflicts that can potentially lead to problems once the data is replicated to the rest of the organization. Proactively monitoring for replication issues can preempt issues that would affect user access and logins.AD is organized hierarchically with domains, Organizational Units, and forests. This structure allows for efficient management and delegation of administrative tasks.
The Global Catalog is a searchable index that contains information about every object in the directory, allowing users and applications to quickly locate resources across the domain. The AD Schema defines all the object types and attributes that can exist in the directory and forest. This schema ensures uniformity and consistency across the AD environment, see: Active Directory Schema (AD Schema) - Win32 apps | Microsoft Learn for details.
LDAP and Kerberos: AD uses the Lightweight Directory Access Protocol (LDAP) for directory services and Kerberos for authentication, providing a robust and secure framework for managing network resources.
Through these mechanisms, Active Directory ensures that users are properly authenticated and authorized, and that network resources are managed efficiently and securely.
Monitoring and troubleshooting Active Directory
We have a number of resources for administrators looking to understand common Active Directory problems and looking for guidance to troubleshoot Active Directory issues. These include:
How eG Enterprise monitors Active Directory
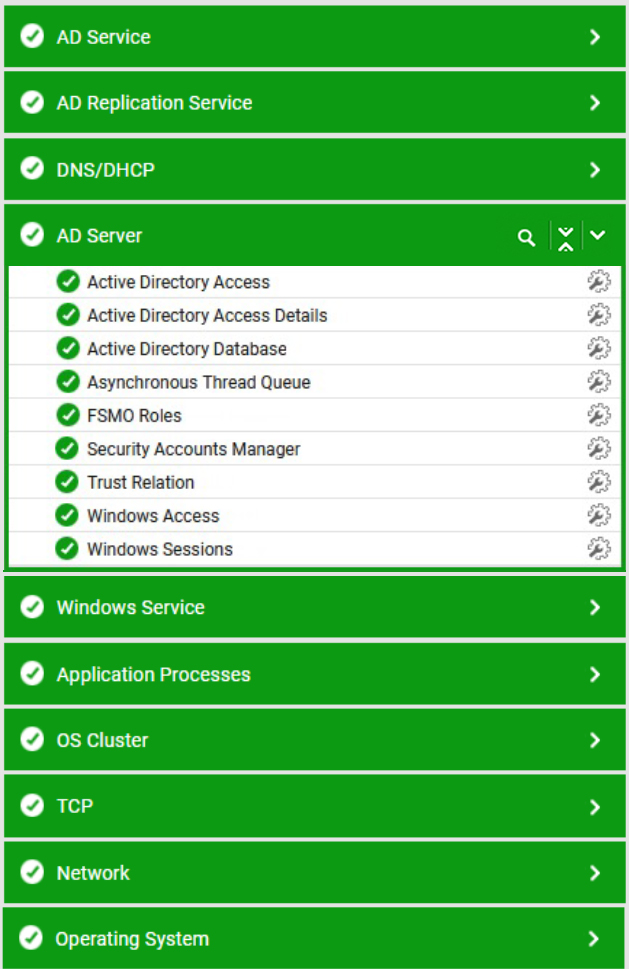
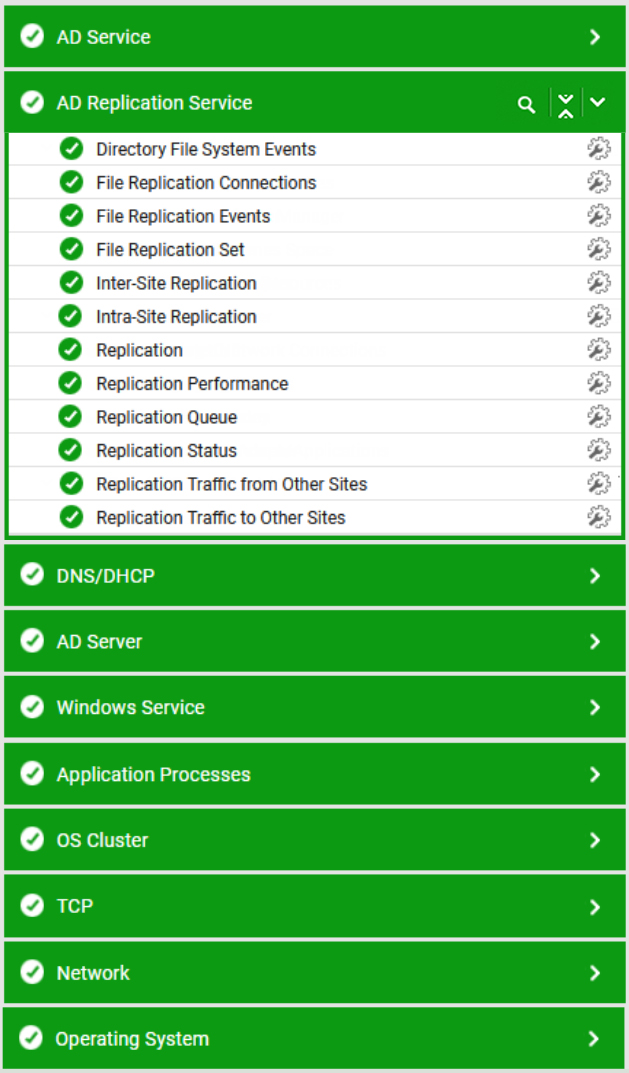
The eG Enterprise platform provides extensive monitoring support for Active Directory servers operating on Windows operating systems. The specialized monitoring model that eG Enterprise offers periodically executes several tests on the AD server to extract a wide range of metrics indicating the availability, responsiveness, and overall health of the AD server and its underlying operating system. Using this model, Active Directory servers can be monitored in an agent-based or an agentless manner.
The powerful AIOps engine within eG Enterprise learns about the IT environment and built-in domain aware intelligence understands the dependencies between AD and the other components of the environment. Metric thresholds and alerting are configured out of the box and AIOps baselining learns about the normal behavior of your AD servers to provide proactive warning of anomalous behavior.
Using these metrics, an administrator will automatically be alerted to problems and is able to find quick answers to performance queries such as:
Continuous monitoring for abnormal login patterns, attempts and failures also enhances the security of your Active Directory servers and IT environment.
Note: how the layer model includes key dependencies such as DNS - If the DNS component of the AD server is unable to provide domain name resolution services, then users may be denied access to their mission-critical servers managed by the AD server. Under such circumstances, you may want to quickly check what is stalling the operations of DNS, so that the source of the issue can be isolated and eliminated.
To learn more about the eG Enterprise platform’s support for Active Directory monitoring, please see: Active Directory Monitoring & AD Monitoring | eG Innovations.
Full details of key metrics, logs and events proactively monitored for Active Directory by eG Enterprise can be found in our documentation, see: Active Directory Monitoring - An introduction (eginnovations.com) (use left-hand menu to navigate the full list of tests).








